Use cases
Intended setup
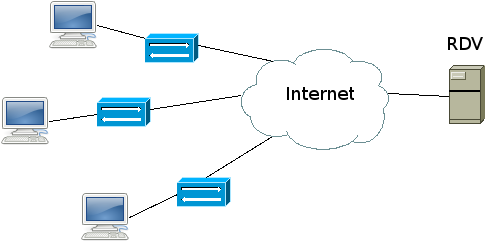
Several clients are connected to Internet. They optionally lie behind a NAT and those NAT must accept UDP hole punching.
The rendezvous server has a public IP or may also be configured behind a NAT. It sees the public endpoints of the clients which is enough thanks to the hole punching.
Corner case 1: common NAT

Here two clients are behind a common NAT. If one sends a packet to the other using its public address, it will fail unless the common NAT does hairpin translation. Sadly hairpin translation is not a widely spread feature.
If both peers enabled the option use_local_addr in their configuration file (which is the default), then the RDV server will tell them to use their local IP to reach each other (the RDV server sees that they both have the same public IP thus are behind the same NAT equipment). This works around the problem and the NAT doesn't need to do hairpin translation. There is no problem with the other peers of the VPN.
Corner case 2: multiple level of NATs
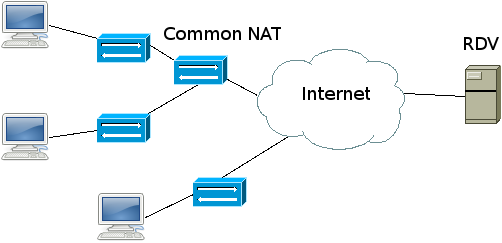
This case involves a common NAT but also at least one peer lying behind another level of NAT.
A first method to connect the two is to disable their use_local_addr option (so that thet won't try to use their private addresses). It will work only if the common NAT supports hairpin translation.
Another method is to use the override_local_addr parameter in conjunction with the use_local_addr parameter explained above. It is used to send a fake local address to the RDV server instead of the real one. So you can define static port forwarding rules on the internal NATs and use this parameter to publish the intermediate IP after the internal NATs.
Corner case 3: rendezvous server and client behind a NAT
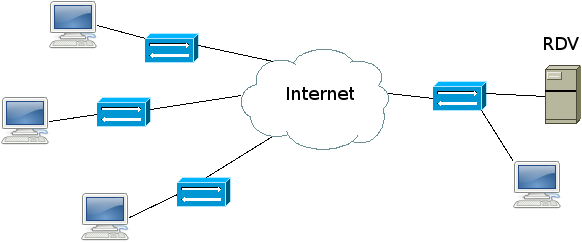
If the RDV server is behind a NAT, you can't run a client behind this NAT neither on the same host nor on another host. It is likely to fail since the RDV server will not be able to see its public address.
Installation
Dependencies
The client requires a recent version of the OpenSSL library. DTLS support was introduced in OpenSSL 0.9.8 but Campagnol requires at least 0.9.8j. The latest version is always a good choice. The client also requires the TUN/TAP driver.
Build
$ ./configure$ make# make install
But you should first have a look at the configuration options with ./configure --help.
If you don't have pkg-config or if you have installed OpenSSL in a non standard directory, you should have a look at the --with-openssl* options. For instance if you want to use an /usr/local based openssl, run:
$ ./configure --with-openssl=/usr/local
If you do not want to build the RDV server or the client, you can use the options --disable-server and --disable-client.
Configuration
You have to edit the configuration file shipped with the client. A few options are mandatory. The configuration file has an INI-like syntax. Comments start with a ';' or a '#' and continue to the end of the line. Values may be quoted between double quotation marks ("...") and special characters can be escaped with '\' (\\, \n, \# ...). The white-spaces around the section names, the parameters and the values are stripped. All names are case sensitive.
See the man page for the meaning of the parameters.
Here is a sample configuration file.
## Campagnol VPN example configuration file## See the campagnol.conf(5) man page for a complete description of the# parameters.#[NETWORK]# Local hostname or IP address# optional# default: search for a non local IP possibly using the "interface" parameter.#local_host = 192.168.0.4# Using 0.0.0.0 will work but is incompatible with the "use_local_addr" option.#local_host = 0.0.0.0# Local UDP port number# optional# default: no port binding#local_port=44556# Allow the use of the local IP and UDP port.# optional# default: yes# This option is useful if this client and other clients of the VPN are behind# the same NAT. See campagnol.conf(5).# Disable this option only if you know that it's not necessary and you know what# you are doing!#use_local_addr = no# Override the local address sent to the RDV server (use_local_address = yes)# optional# default: not enabled# In some special case, it may be usefull to use another address (for example# the public address on a NAT) instead of the real local address. See# campagnol.conf(5).#override_local_addr = 172.16.17.17 23456# Rendezvous server hostname or IP address# mandatoryserver_host = 192.168.0.1# Rendezvous server port# optional# default: 57888#server_port = 34567# MTU of the TUN device# optional# default: 1419# This parameter must be the same for all peers# It may be interesting to change the MTU of the tun device if# you are running campagnol on a network with a unusual MTU.#tun_mtu = 1400# Use a specific network interface# optional# This parameter is used to find the local IP address to use if the "local_host"# parameter is not set.# Linux only: if given, the UDP socket is bound to this interface.# default: no interface binding#interface = eth0# Linux:# Give the name after-specified to the TUN device.# default: the interface is named tun%d# Cygwin:# The name of the TUN/TAP adapter to open.# default: open the first TUN/TAP adapter found.# Other OS: this parameter is ignored.#tun_device = "Local Area Connection 3"# Cygwin only:# The name of the OpenVPN's TUN/TAP driver.# This is used to search for TUN/TAP adapters.# default: tap0901# It may work with other versions.#tap_id = "tap0801"[VPN]# IP address for the VPN# mandatoryvpn_ip = 10.0.0.1# Subnetwork for the VPN# mandatory# must be the same for all peers# Use the CIDR notationnetwork=10.0.0.0/24[SECURITY]# PEM file containing the client X.509 certificate# mandatorycertificate = ./box1/certificate.pem# PEM file containing the client private key# mandatorykey = ./box1/key.pem# PEM file containing a root certificates chain# Specify at least one of ca_certificates and ca_cartificates_dirca_certificates = ./box1/cacert.pem# Directory containing root certificates.# It must have been prepared by the c_rehash OpenSSL's utility.# Specify at least one of ca_certificates and ca_cartificates_dir#ca_certificates_dir = ./box1/root_certs/# PEM file containing a certificate revocation list (CRL)# optionalcrl_file = ./box1/crl.pem# Maximum depth for the certificate chain verification.# optional# default: 9#verify_depth = 1# The OpenSSL ciphers lists to use# optional# default: OpenSSL's default# must be the same for all peers# See openssl ciphers man page for more details# For RSA, cipher suites with key lengths larger than 128 bits, sorted by# strength:#cipher_list = RSA+HIGH:@STRENGTH# For Camellia, 128-bit key, RSA and SHA1:#cipher_list = CAMELLIA128-SHA# For no encryption:#cipher_list = NULL[CLIENT]# Internal FIFO size# optional# The client uses one FIFO per connected peer# default: 20#fifo_size=50# Linux only:# Length of the TUN/TAP driver's transmit queue# optional# This sets the length of the internal transmit queue on the TUN device.# default: 500 frames (current default of the TUN/TAP driver)#txqueue=100# Linux only:# Use the TUN/TAP driver in single queue mode.# optional# This instructs the TUN/TAP driver to use its single queue mode. This is# required to work around a bug in pre-2.6.11 kernels. It can also helps with# slow hardware or slow connections by reducing the total TX queue length.#tun_one_queue=yes# Bandwidth throttling# optional# default: disabled# Those two options allow to limit the outgoing traffic for the whole client# and/or for each connection. The values are in kilobytes/seconds.# Comment one option to disable it or use 0.# Limit the outgoing traffic to 500 kB/s and/or allow 100 kB/s per# connection:#client_max_rate = 500#connection_max_rate = 100# Inactivity timeout before closing a session.# optional# The value is given in secs (integer)# default: 120 seconds#timeout = 120# Period of inactivity before sending a keepalive message# optional# default: 10 seconds#keepalive = 30# Maximum number of connections with other clients# optional# default: 100#max_clients = 20[COMMANDS]# Execute the default commands to configure the TUN device# optional# default: yes# If this is set to no, the commands are specified with the "up" parameter.#default_up = no# Execute the default commands when the TUN device is closed.# optional# default: yes# If this is set to no, the commands are specified with the "down" parameter.#default_down = no# Add a shell command to execute when the TUN device is configured and# default_up is false.# The following special values are available:# %D - the tun device# %V - VPN IP# %M - MTU# %I - local IP# %P - local UDP port# %N - Netmask# %n - Netmask, in dot-decimal notation# %% - the '%' char#up = "echo configuring %D!"# Default programs for Linux:#up = "ifconfig %D %V mtu %M up"#up = "ip route replace %N via %V || route add -net %N gw %V"# For FreeBSD and NetBSD:#up = "ifconfig %D inet %V %V mtu %M up"#up = "route add -net %N %V"# For OpenBSD (you do not need to setup the MTU with ifconfig, it's already# done):#up = "ifconfig %D inet %V %V up"#up = "route add -net %N %V"# For Cygwin (you do not need to setup the MTU, it's already done):#up = "netsh interface ip set address name=%D static %V %n none"# Add a shell command to execute when the TUN device is closed and default_down# is false.# The same special values are available.#down = "echo closing %D!"# There is no default down command on Linux, OpenBSD and Cygwin.# Default command for FreeBSD and NetBSD:#down = "ifconfig %D destroy"
Creating the certificates
Using the ca_wrap script
Campagnol comes with a small wrapper script around the OpenSSL utilities. It can be used to:
- create a basic OpenSSL configuration file
- build the root certificate authority key and certificate
- create new keys and signed certificates for your VPN
- revoke certificates
- generate a certificate revocation list
You first need to create the directory for your CA and to copy the script into this directory. Then you must edit the script to setup its working direcory and the default fields for the generated certificates.
Once the script is configured, create the configuration file for OpenSSL:
./ca_wrap.sh gen_conf
Then you have to create the private key, the root certificate and all the required files:
./ca_wrap.sh gen_ca
For each client on the VPN, you will have to create a new key/certificate:
./ca_wrap.sh gen_cert my_client./ca_wrap.sh gen_cert other_client
You can also revoke an old certificate and generate a revocation list:
./ca_wrap.sh revoke_crt my_client./ca_wrap.sh gen_crl
Sample certificates
The samples directory in the client sources contains a few certificates useful for testing purpose only.
Running
Rendezvous server
Run the rendezvous server on a publicly accessible computer (for every clients of the VPN). The server uses the default UDP port 57888. Be sure that this port is reachable. The server doesn't require superuser privileges if you do not ask for a privileged port (<1024).
The rendezvous server accepts up to 100 registered clients by default.
Start the server and adjust the maximum number of registered clients:
campagnol_rdv --max-clients=20
To start the server on another port:
campagnol_rdv --port=34567
To start the server as a daemon:
campagnol_rdv --daemon
Client
To start a client, run:
campagnol conf_file.conf
To start the client as a daemon:
campagnol --daemon conf_file.conf
Send a SIGTERM or SIGINT signal to the client to kill it cleanly. If no configuration file is given, campagnol will search for a default /etc/campagnol.conf file. When campagnol is launched as a daemon, it will write its PID into /var/run/campagnol.pid (or another file defined in the configuration).
If you changed the CRL or the key/certificate used by a client, you can use:
- SIGUSR1 to immediately kill all the connections and reload the files
- SIGUSR2 to smoothly reload the files (they will be used for the subsequent connections)
